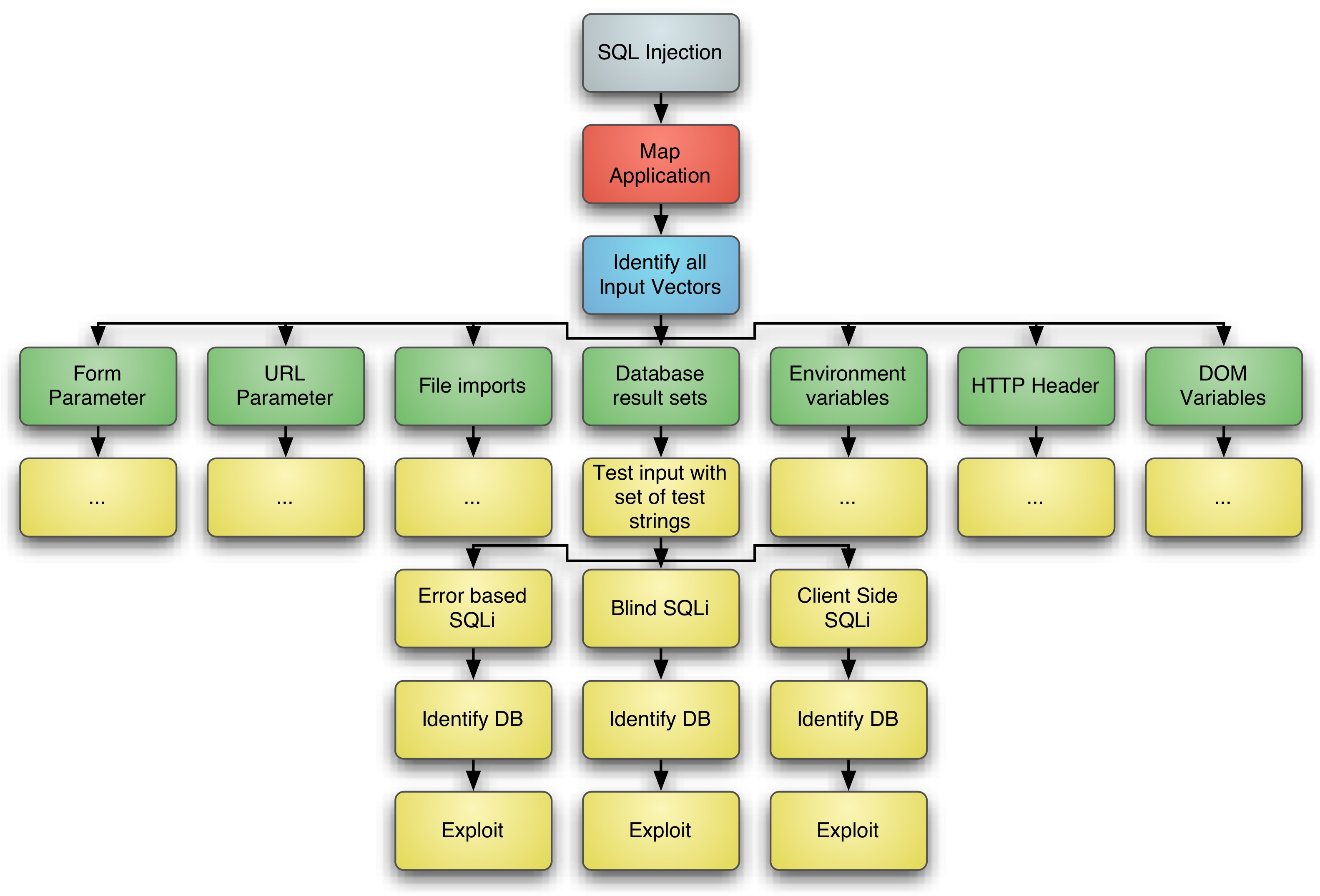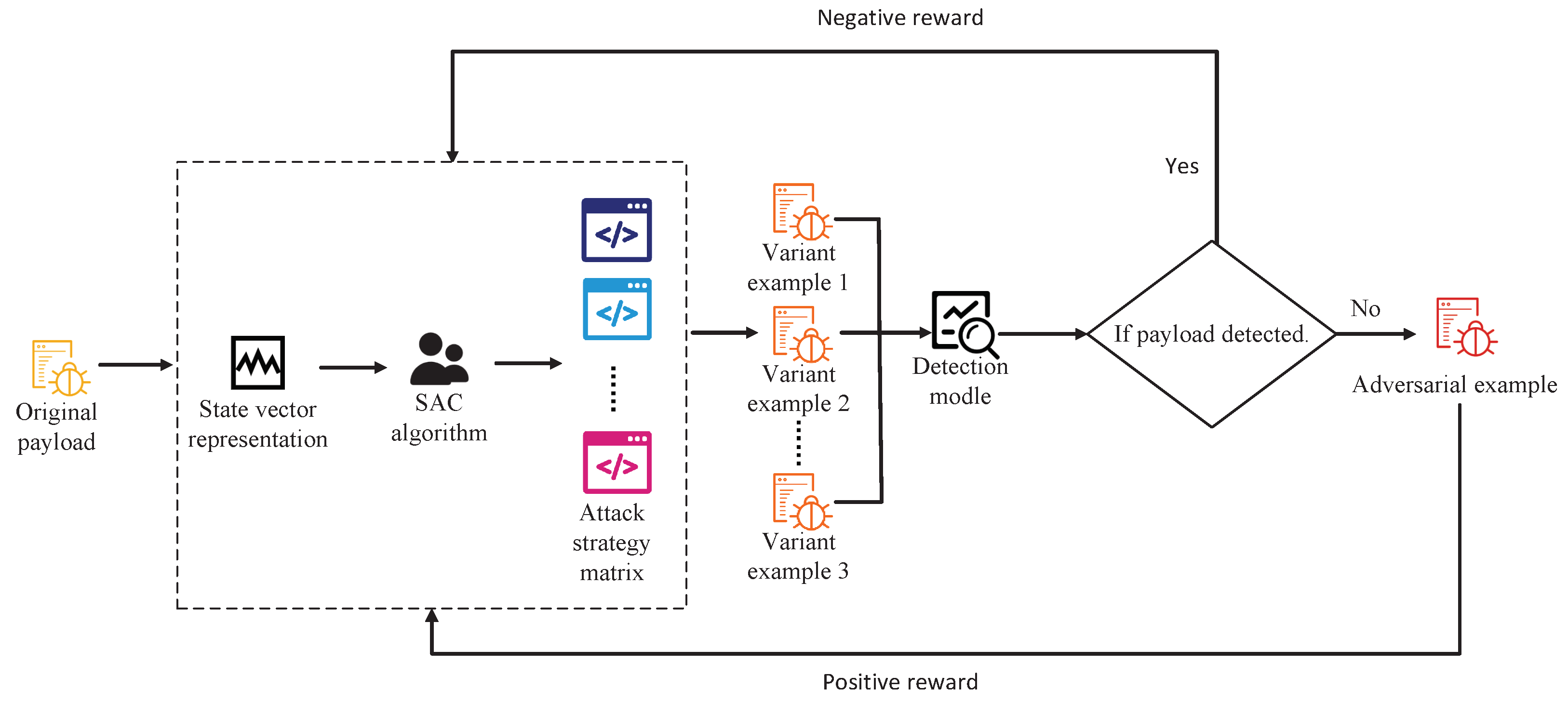
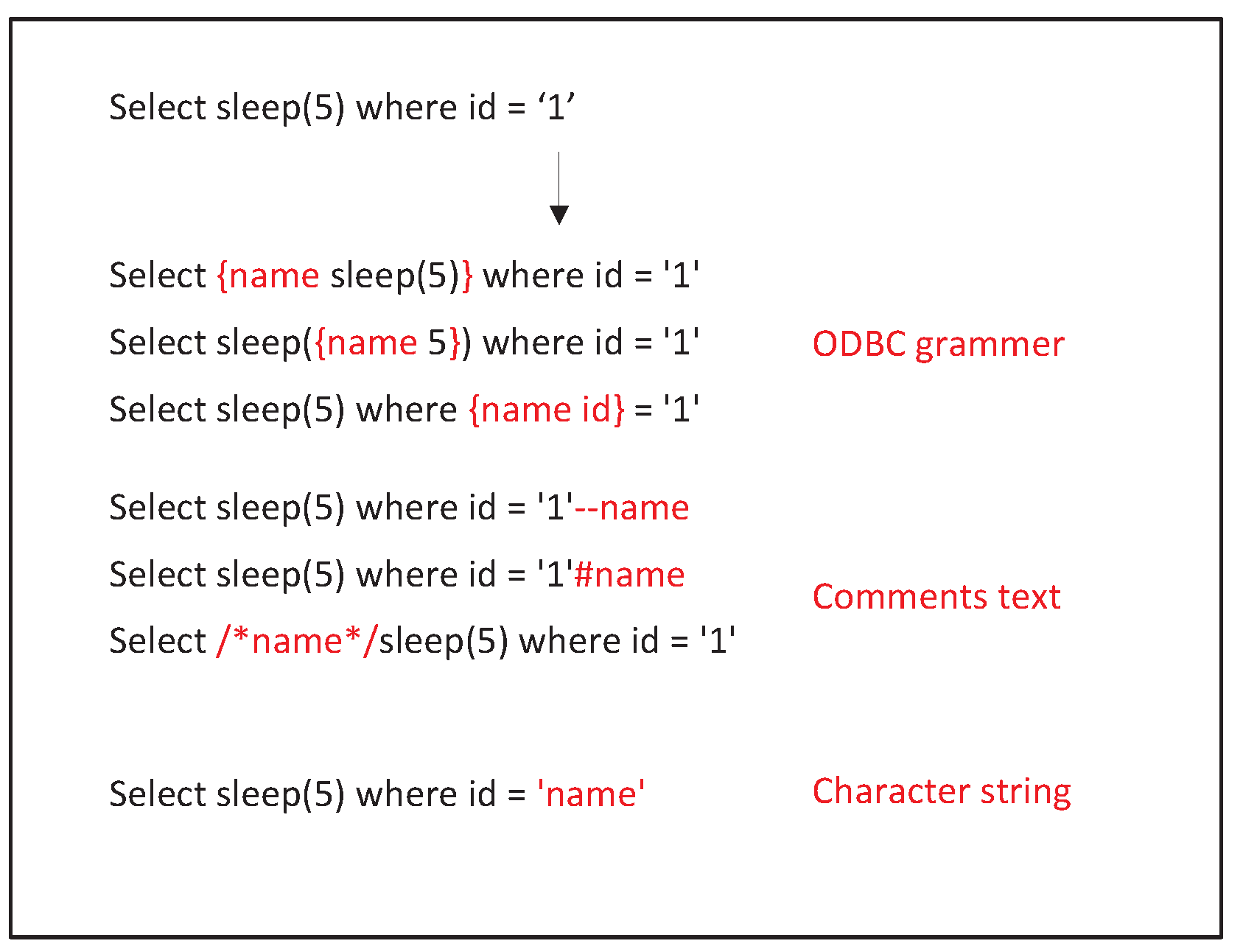
Future Internet | Free Full-Text | SSQLi: A Black-Box Adversarial Attack Method for SQL Injection Based on Reinforcement Learning

Art of Software Security Testing, The: Identifying Software Security Flaws eBook : Wysopal, Chris, Nelson, Lucas, Dustin, Elfriede, Dai Zovi, Dino: Amazon.in: Kindle Store

PDF) SQL injection detection and prevention system with raspberry Pi honeypot cluster for trapping attacker

Learn How Hackers Find SQL Injections In Minutes With Sqlmap | SQL, database | SQLmap has proven to be one of the best tools to test database security. You must be aware


![4K] Cybersecurity Programming: Build SQL Injection Scanner with Python - YouTube 4K] Cybersecurity Programming: Build SQL Injection Scanner with Python - YouTube](https://i.ytimg.com/vi/HJBxn8KZRuM/maxresdefault.jpg)



![Set Up a Vulnerable Target Computer with DV-Pi (Damn Vulnerable Pi) [Tutorial] — SkyNet Tools Set Up a Vulnerable Target Computer with DV-Pi (Damn Vulnerable Pi) [Tutorial] — SkyNet Tools](https://skynettools.com/wp-content/uploads/2020/10/Set-Up-a-Vulnerable-Target-Computer-with-DV-Pi-Damn-Vulnerable-1024x576.jpg)