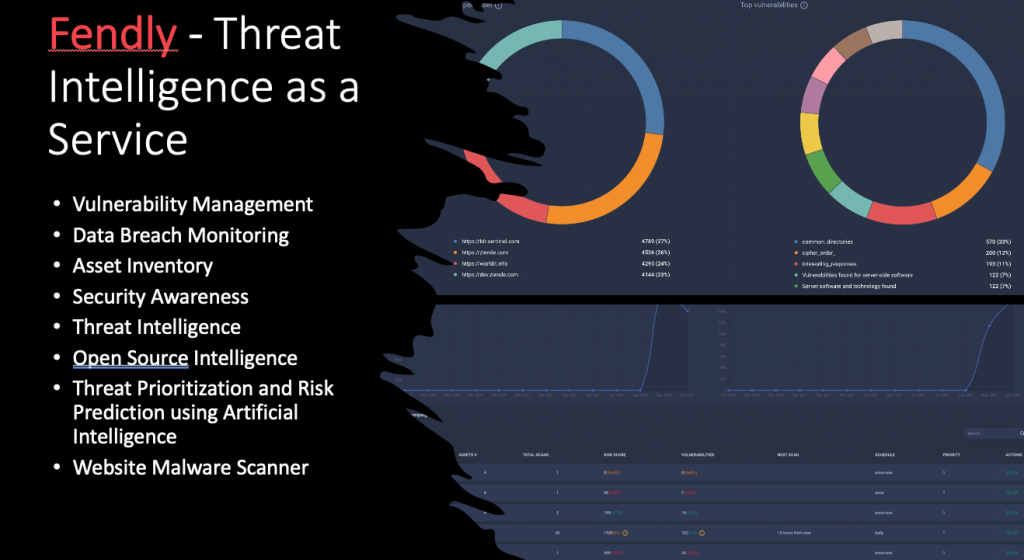
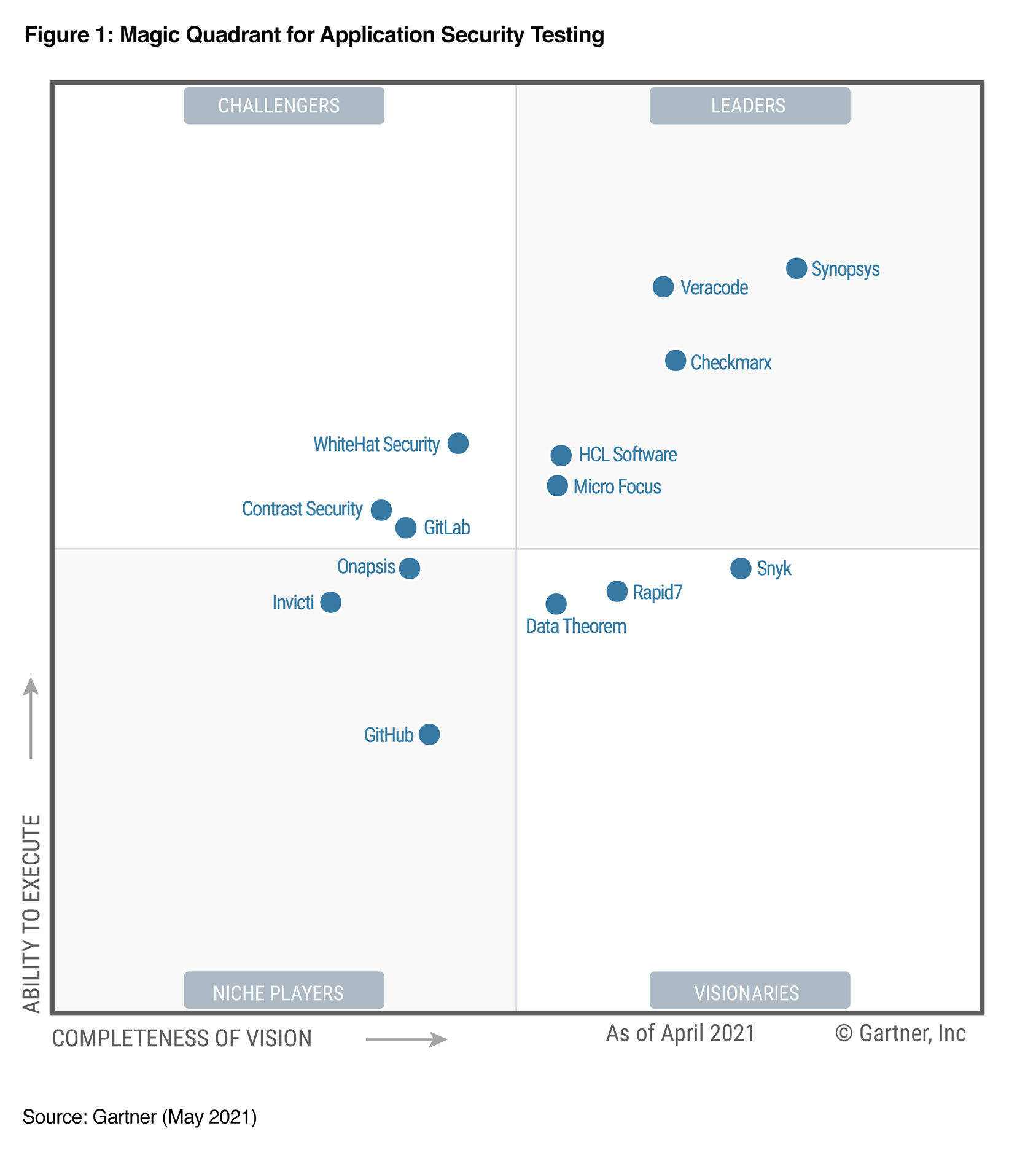
Streamline your AppSec with application security orchestration and correlation | Nixu Cybersecurity.

Sniper – Automatic Exploiter from Pentest-Tools.com (“Best Emerging Technology” finalist at SC Europe Awards 2022) - DefCamp 2022
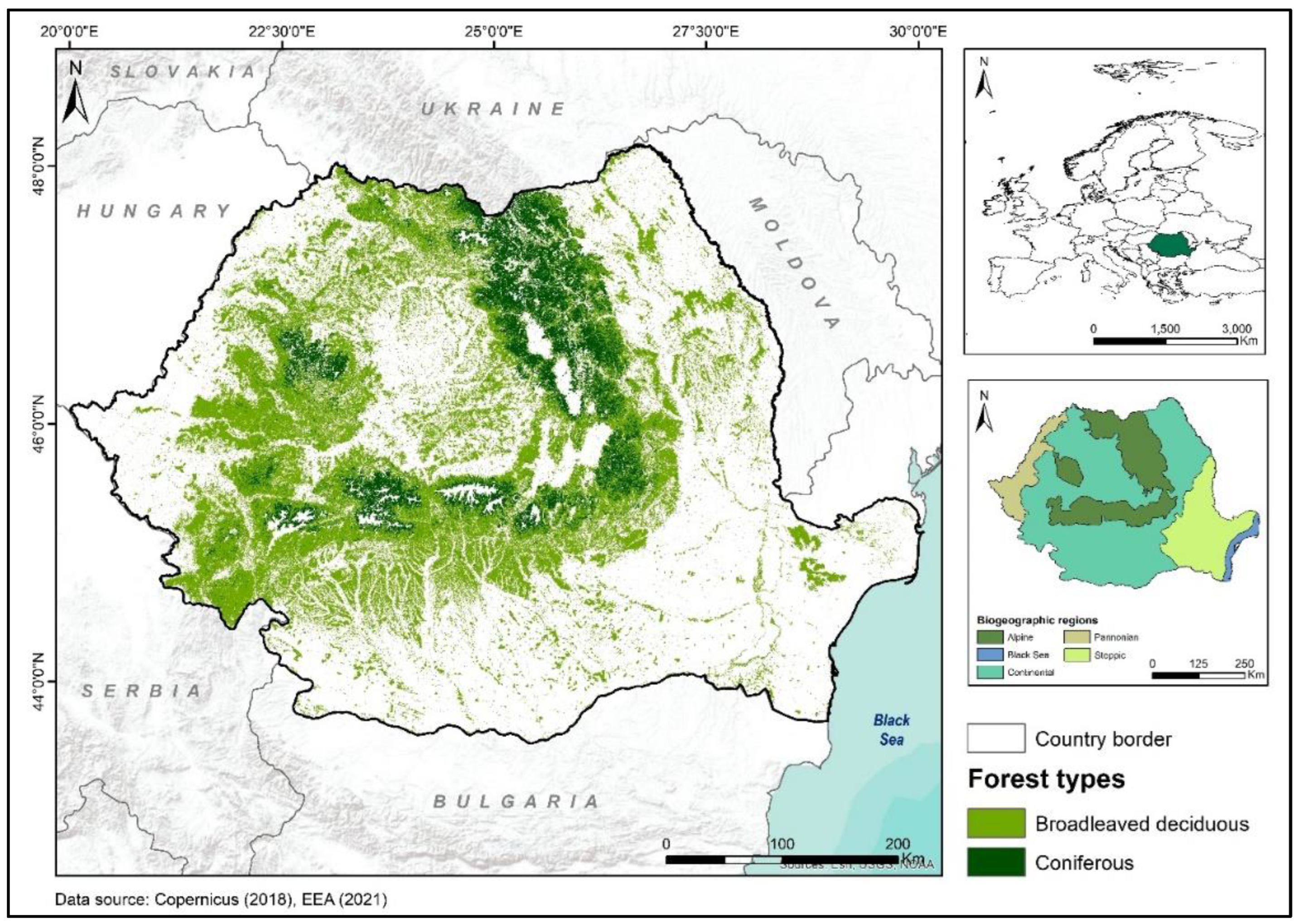
Land | Free Full-Text | The Winding Road towards Sustainable Forest Management in Romania, 1989–2022: A Case Study of Post-Communist Social–Ecological Transition




/filters:no_upscale()/news/2022/12/google-osv-scanner/en/resources/1Screen%20Shot%202022-12-12%20at%203.12.11%20PM-1671726707795.png)