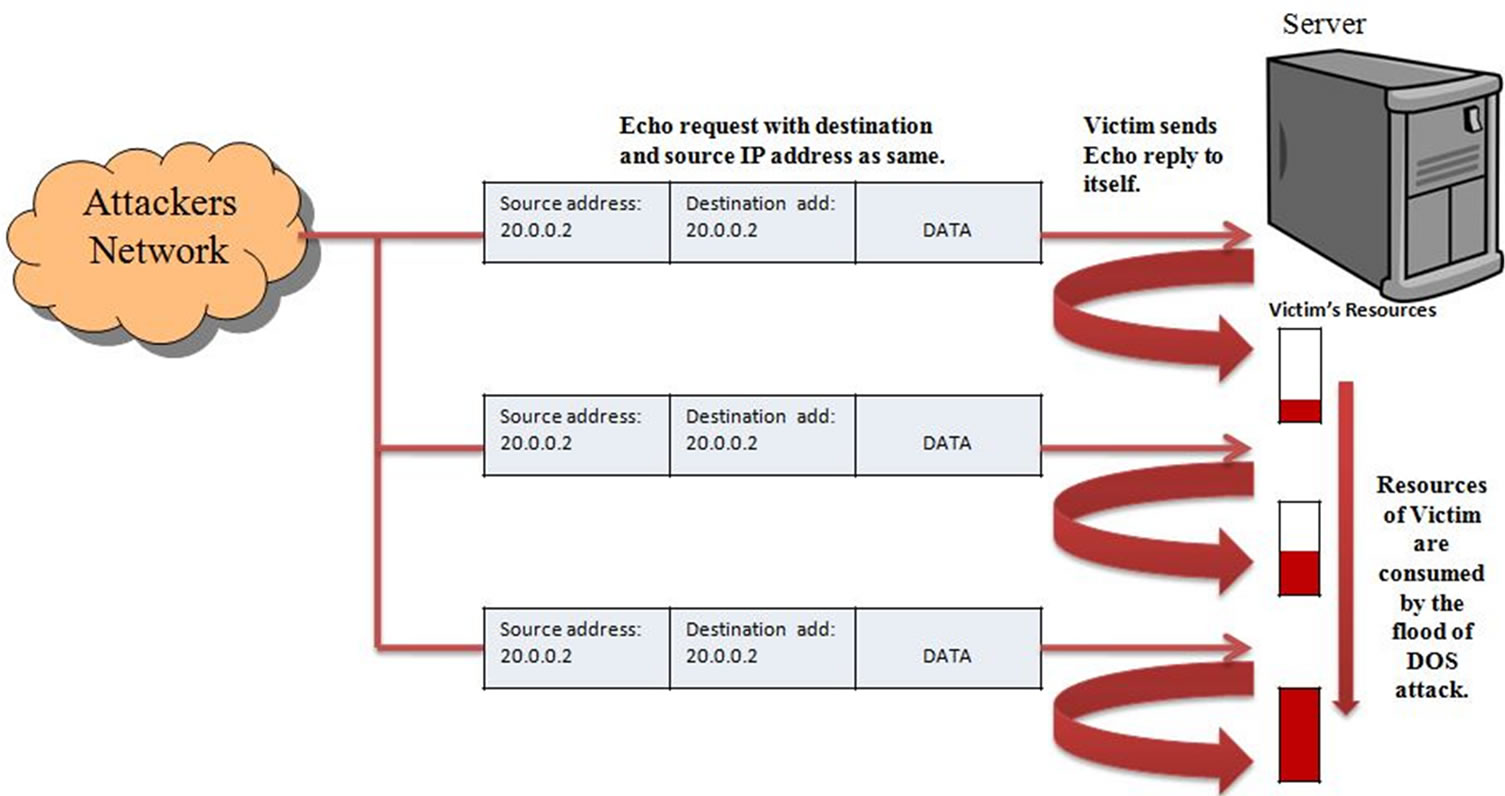
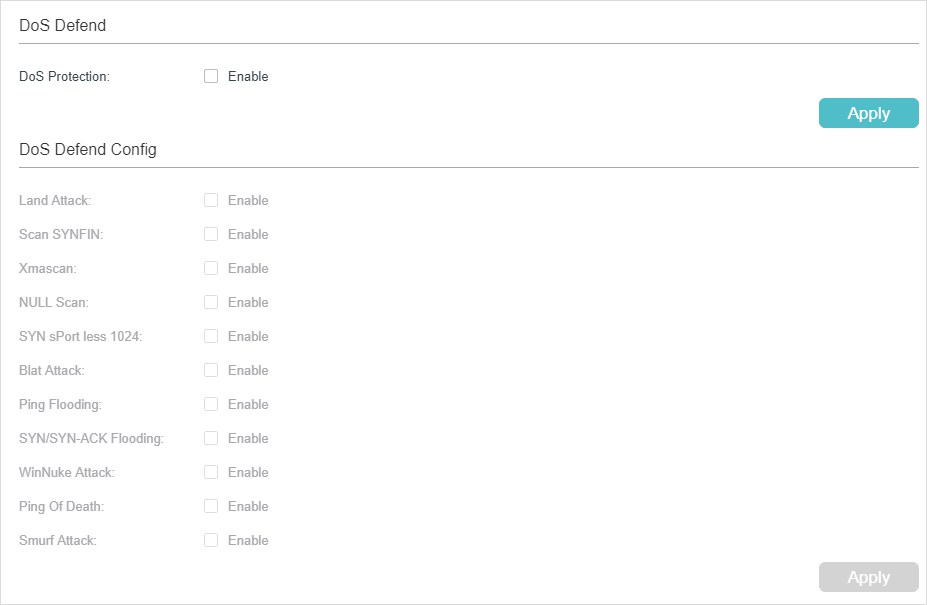
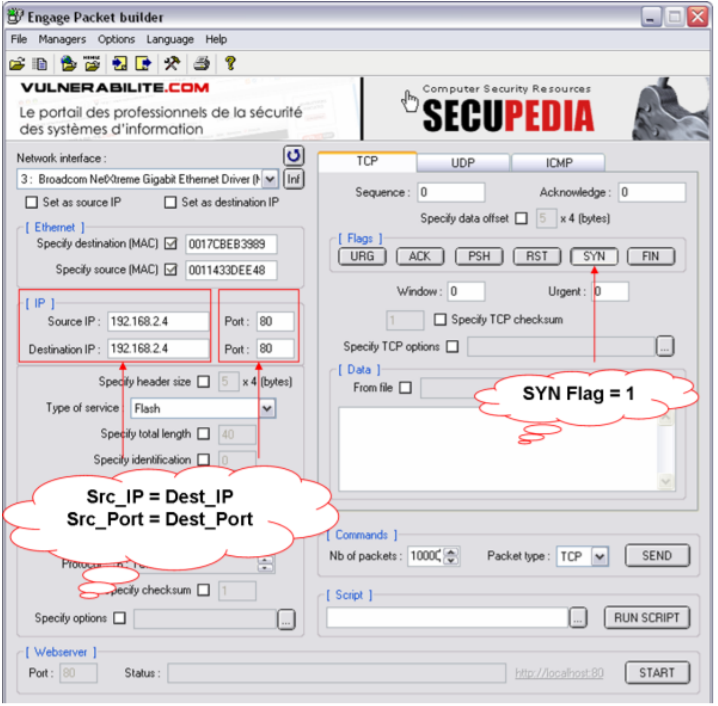
An example of a Land attack packet A packet generator tool can be used... | Download Scientific Diagram

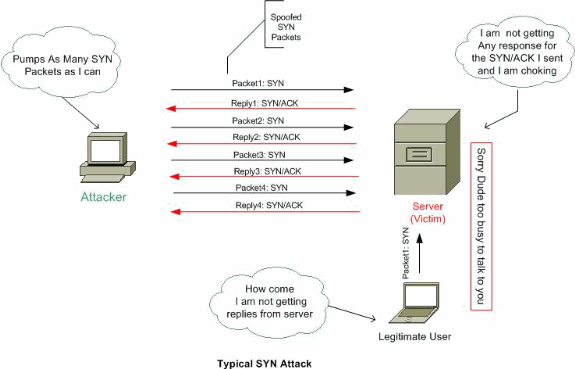
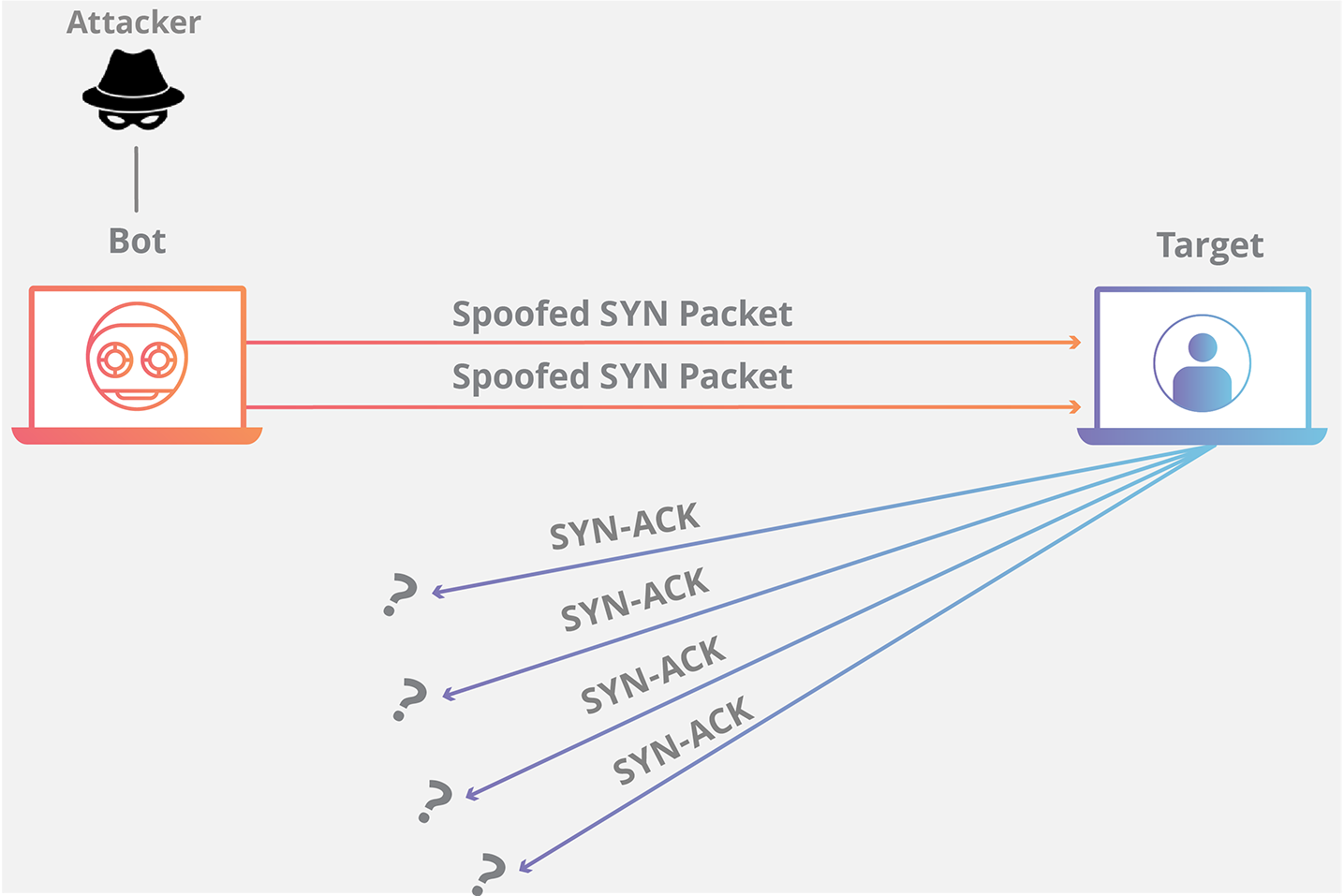
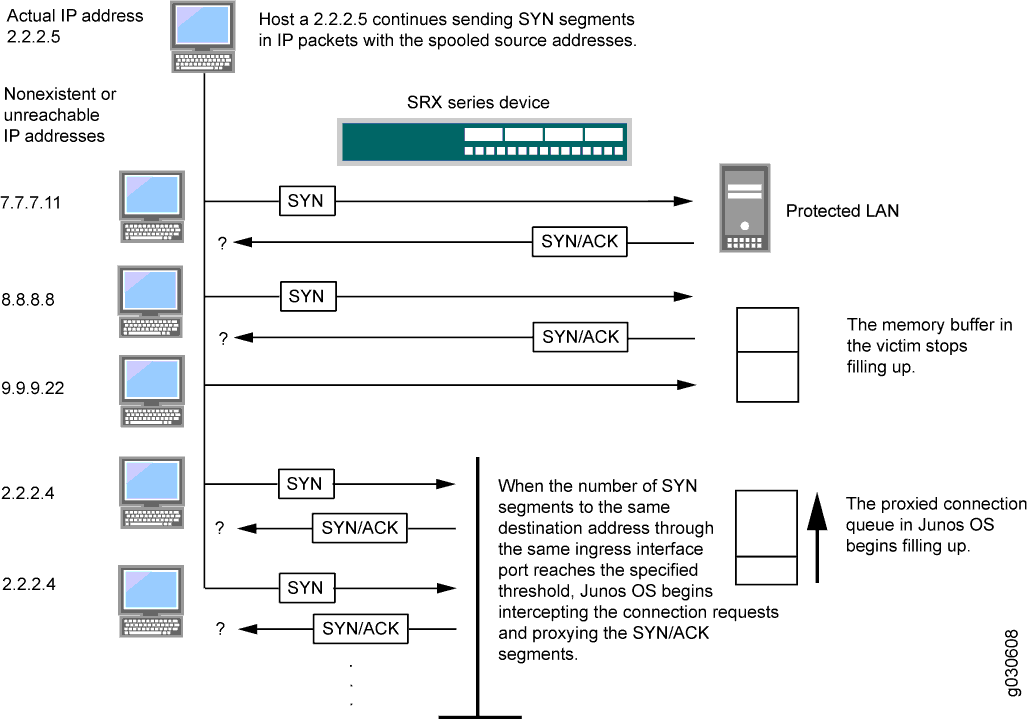
The TCP SYN flood attack Hands-on lab exercise on TCP SYN flood attack | Download Scientific Diagram

TurkHackTeam EN on Twitter: "Land Attack❗ #cybersecurity #cyberattack #data #attack #attacker #system #machine #network #tcp #ip #dos #ddos #land #web #website #files #cybercrime #hack #hacker #hacking #turkhackteam https://t.co/fpY9A4MfKr" / Twitter

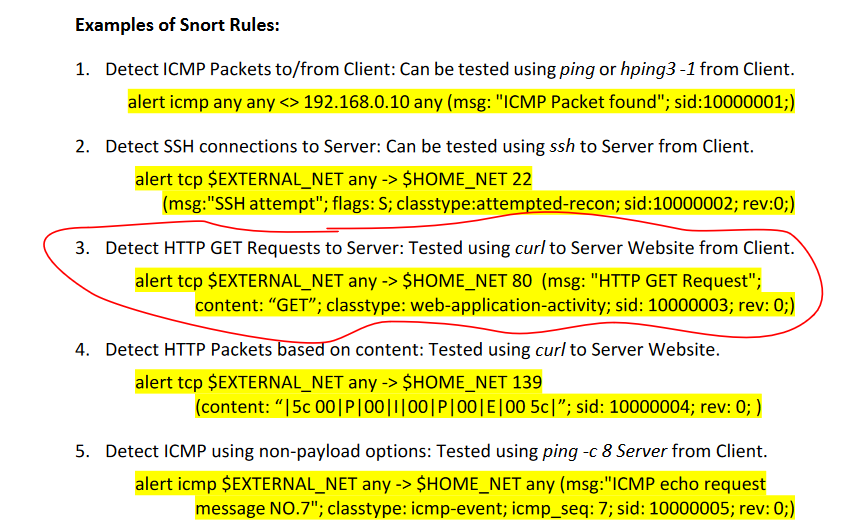
Attack Defense - AR120, AR150, AR160, AR200, AR1200, AR2200, AR3200, and AR3600 V200R007 CLI-based Configuration Guide - Security - Huawei