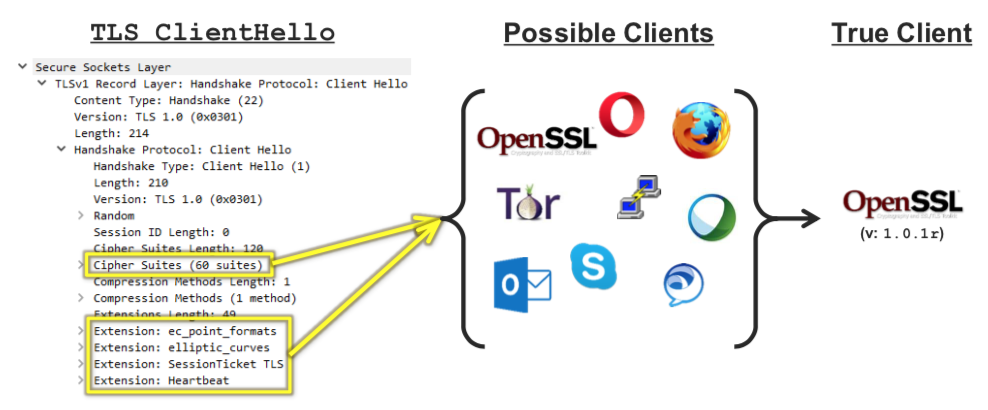
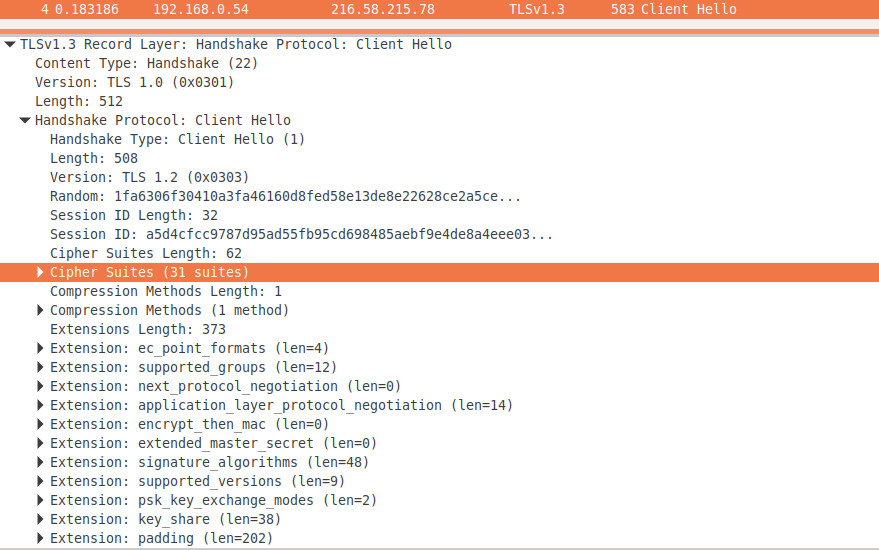
GitHub - salesforce/ja3: JA3 is a standard for creating SSL client fingerprints in an easy to produce and shareable way.

Kevi "Fauda" Agit, Kurdish explosive expert and new Merc in JA3. Her character looks great, we are yet to hear her voice. As pointed by a fan, the flag in her bio


-1.png)