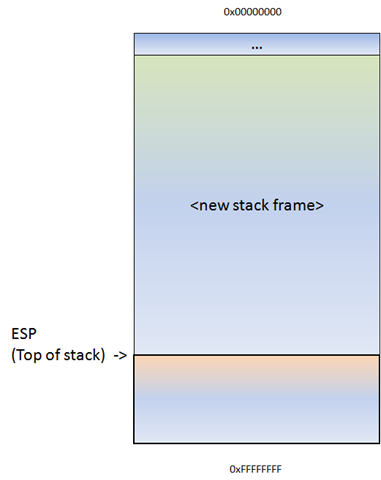
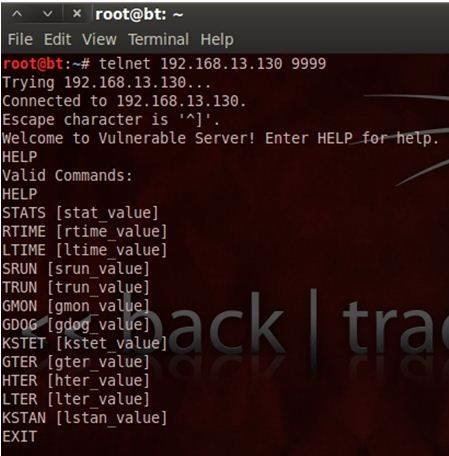
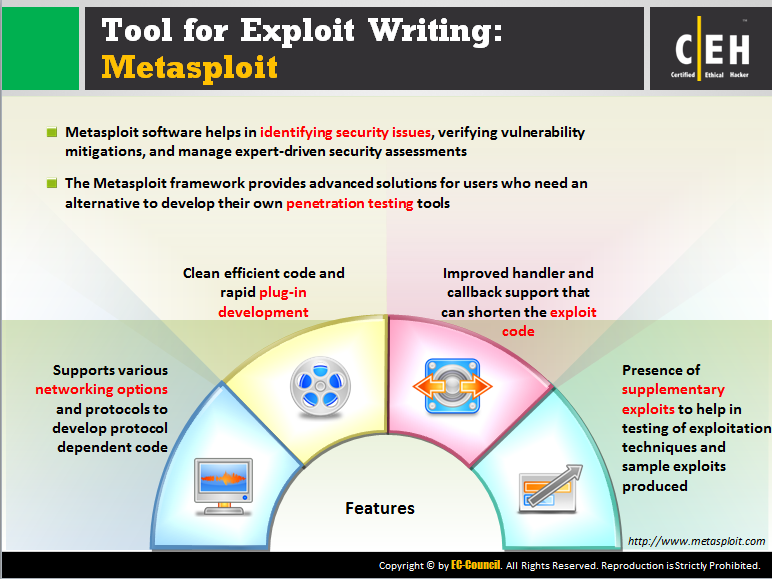
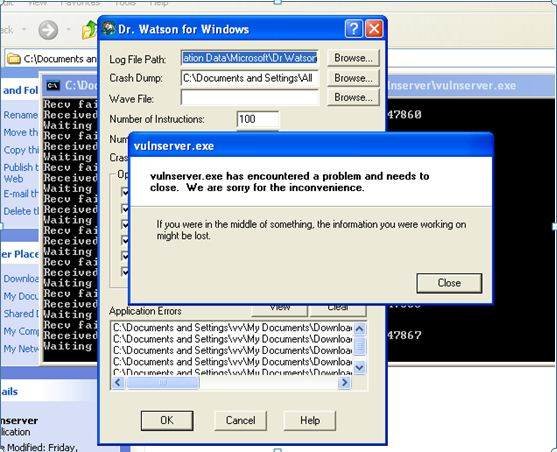
J. Imaging | Free Full-Text | Intraoperative Gamma Cameras: A Review of Development in the Last Decade and Future Outlook

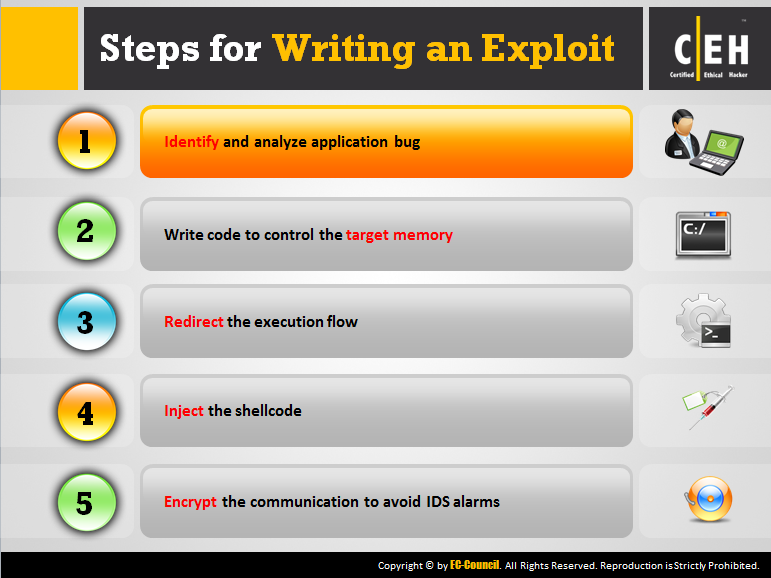
Exploit Writing | CTG Infosec - Ethical Hacking | Web Security Expert | Network Security Expert |Bug Bounty |Source Code Review |Reverse Engineering | Exploit Development | Malware Analysis |Mobile Application Security